Legislation ICT Authority's proposal to monitor the Internet, in a nutshell
The Information and Communication Technologies Authority published a Consultation Paper on 14 April 2021 which contains proposals to amend the ICT Act. The ICT Authority proposes two frameworks and a set of tools to decrypt and archive traffic on social media platforms for inspection purposes.

The Information and Communication Technologies Authority (ICTA) invites the public to comment on a Consultation Paper on amendments to the ICT Act which the authority proposes in order to regulate Social Media in Mauritius.
I read the Consultation Paper and in my humble opinion the authors of the paper could not define the problem they want to address.
In Section 3.1 they mention incidents that happened in Myanmar and India based on rumours on WhatsApp and Facebook. Relating issues in Mauritius, the authors mention in Section 3.3 that « we » which I assume to be law enforcement officers face a language barier when reporting offensive and abusive content posted in creole. They mention that in majority of the cases complaints made by local authorities to the social media administrators remain unattended or are not addressed in a timely manner.
It is unclear whom the authors are calling "social media administrators", whether administrators of individual groups/pages on social media platforms or the operators of the service.
There is no mention of any specific case that disturbed social harmony and where social media companies did not collaborate or were slow to respond to the requests of local authorities. The only local data which is shared is a table of incidents reported via the Mauritian Cybercrime Online Reporting System (MAUCORS). The paper mentions a total of 2,051 incidents reported between January 2020 and January 2021.
However, these are incidents reported via an online tool. No further information is provided about specific cases or how many of these online reported incidents were formally lodged, investigated and people prosecuted. Also, what were the difficulties when investigating or prosecuting, whether social media companies did not cooperate etc?
Anyway, half of the 24 pages document talks a lot with no verifiable data in Mauritius on actual cases and yet their conclusion to the « problem » can be summed up as follows:
- local authorities should be able to block harmful & illegal content on social media without the intervention of social media companies,
- local authorities should be able to identify people who post on social media platforms without the intervention of social media companies.
In order to achieve the above, the authors propose to amend the ICT Act to do three things.
- set up a committee called the National Digital Ethics Committee (NDEC), which will comprise of people who will decide what can be deemed « harmful » on the Internet,
- set up a technical unit called the Technical Enforcement Unit, which will comprise of ICTA staff personnel who will operate the technical infrastructure of monitoring Internet traffic in Mauritius,
- deploy an Internet monitoring infrastructure that will intercept all incoming/outgoing Internet traffic in Mauritius, segregate social media traffic, decrypt the traffic and archive the data for inspection purposes and encrypt the traffic again.
I am not going to focus on the flaws with the NDEC & Enforcement Unit proposals. Let us instead look at what will the technical implementation of this monitoring infrastructure look like.
In a nutshell
ICTA wants to peek into your social media traffic. How can they do that since your social media traffic is encrypted? Let's see.
If the proposed amendments are passed as law and the ICT Authority deploys their Internet monitoring infrastructure, this is what will happen.
- You will type facebook.com in your browser but the request won't go to the Facebook servers.
- The request will go to the ICTA proxy server.
- The proxy server will in turn take your browser's request and forward it to the Facebook servers.
- When Facebook returns the login page, it also returns the necessary cryptographic information to start a secure connection using a username & password.
- ICTA's proxy server will present you the facebook.com login page with the HTTPS padlock shown in the brower's address bar.
- When you enter your username and password and press enter, they will be encrypted and sent to the ICTA's proxy server which has the key to decrypt this information.
- The proxy servers reads your username & password, makes a copy and archives it for inspection purposes.
- The proxy server then re-encrypts your username & password using the cryptographic information Facebook sent it earlier and sends the encrypted data to facebook.com.
- Facebook decrypts it, confirms your username & password, and grants the proxy server access to your Facebook account.
- The proxy server decrypts the answer from Facebook, copies it and archives the same, and then re-encrypts the page before sending it to your browser.
- This process continues for all transactions between your browser and Facebook, thus allowing the ICT Authority's proxy server to make a copy of everything you do on Facebook.
How does an encrypted communication with Facebook looks like normally?
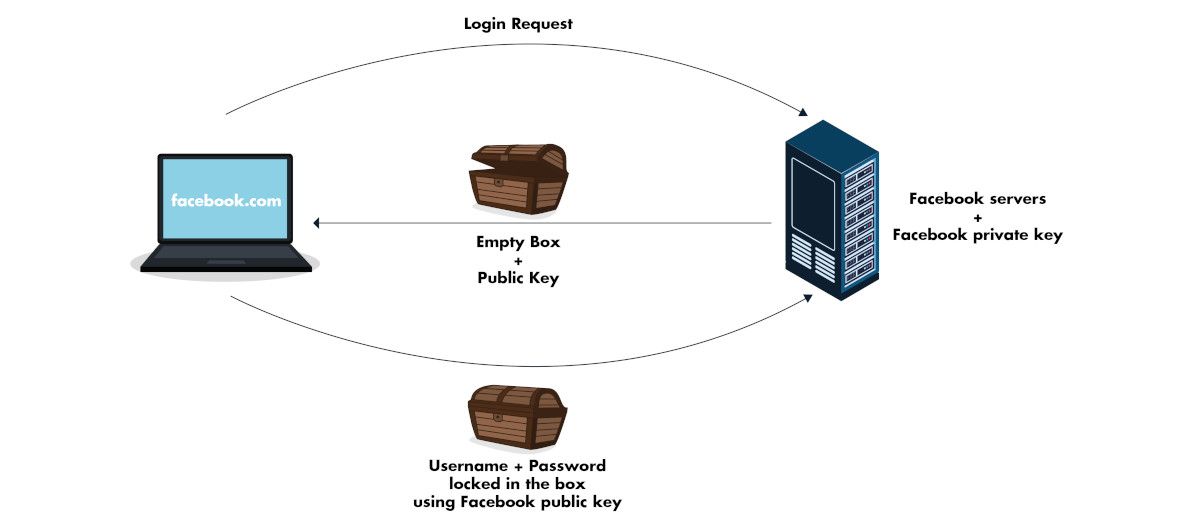
You make a request to facebook.com, Facebook servers return you an empty box and a public key. You put your username/password inside the box and lock it with the public key. You send the locked box back to Facebook. Now, this box can only be opened with the private key on the Facebook servers and no one else. If someone alongs the way copies the box, it will be useless because the box won't open.
How does an encrypted communication with Facebook in ICTA's new world will look like?
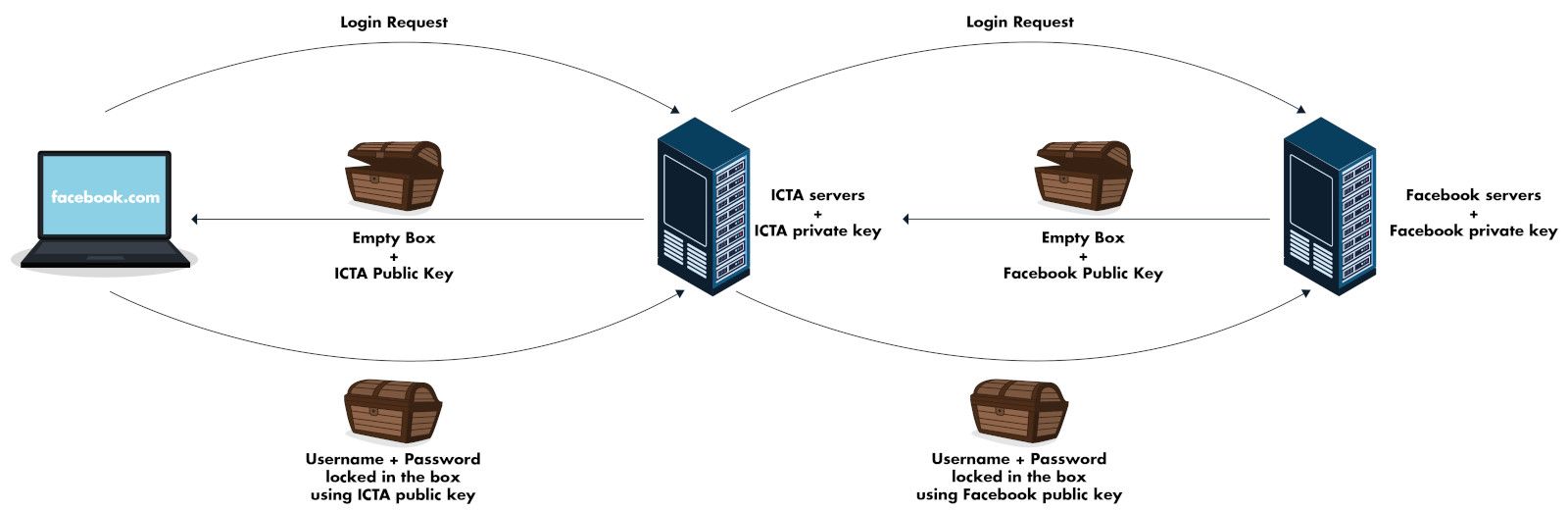
You make a request to facebook.com and the ICTA proxy server sends you an empty box and a public key. Your browser trusts this « facebook.com » which in fact is the ICTA proxy server because it trusts the certificate presented by the proxy server. We will explore this detail later. Now, you put your username/password in the box, lock it with the public key you obtained and send it the ICTA proxy server. The latter unlocks the box with its private key, makes a copy of the data, i.e your username/password. It then puts your username/password in another box which Facebook sent it and locks it with Facebook's public key. Finally, Facebook unlocks the box and confirms your username/password and the rest of the communication follows the same process ensuring every bit of information being copied at the ICT Authority's proxy server.
In cybersecurity terms this is called a Man-In-The-Middle attack, whereby an attacker relays information between two parties who believe they are communicating with each other directly.
Art of deception
For the ICTA proxy server to be able to do this it has to impersonate you when communicating with Facebook and it impersonates Facebook when it communicates with you.
To allow such a deception the ICT Authority will ask you to install a Certification Authority (CA) certificate in your browser. Once you do so, your browser will trust all websites that the ICTA proxy server impersonates.
What happens if you do not install the certificate?
Your browser will tell you that the website you are visiting poses a risk and it will discourage you from continuing. If you decide to accept the risk and continue visiting the site it means you have granted your browser permission to establish a connection with the proxy server despite the risk. Thereafter, everything's the same as specified above. If you neither install the certificate nor accept to continue with a risky & untrusted connection, then you won’t be able to visit the websites that the NDEC decide to actively monitor & regulate.
I specifically did not mention VPN services or Tor because the proposed amendments should simply not pass as law. We should not be talking about how to bypass the infrastructure but rather explain to more people about the implications of these amendments and encourage them to send their comments to socialmediaconsultation@icta.mu by latest 5 May 2021 at 16h00.
You can read comments to the ICT Authority here.
Encrypted communication illustration made by Shelly using icons by freepik.
Cover photo by dole777 on Unsplash.