Mauritius Proof-of-concept proxy shows user account passwords and private photos can be decrypted
A proof-of-concept proxy using Fiddler Everywhere shows that user account passwords from websites like Twitter, LinkedIn, Gmail Hotmail and private photos from Facebook, Messenger and Instagram can be decrypted.
Since the publication of ICTA’s consultation paper1 on proposed amendments to the ICT Act in order to regulate social media, there has been an outcry and a lot of criticism on the measures proposed. Professionals from the ICT industry have raised alarms over the security risks that the proposed technical framework will give rise to. Legal professionals and civil society activists have expressed that the measures are radically dis-proportionate to the problems stated. The proposed measures will heavily affect the individual’s privacy rights.
ICTA issued several communiques2 in an attempt to dispel fear and doubt surrounding their proposal. However, those communiques repeatedly stressed only public posts on Facebook will be filtered and decrypted.
For example, in a recent video3 published on ICTA’s website, at 2m3s, they say that ICTA won’t get user password, log in, email, private messages, bank details etc.
In this report, I explain how a proof-of-concept proxy was used to demonstrate the capabilities of the technical framework proposed in Section 11.2 of the consultation paper.
Disclaimer:
The purpose of this report is purely educational and written to demonstrate a specific context. Any misuse of the knowledge of the software or technique described in this report cannot be held against the author, i.e Ish Sookun. If you continue to read, you acknowledge having read this disclaimer.
ICTA's Proposed Technical Framework
These three steps are the most important ones that are mentioned in Section 11.2 of the consultation paper and my proof-of-concept will focus on these steps only.
- install a Certification Authority (CA) root certificate in web browser,
- route requests for facebook.com to a proxy server,
- decrypt the HTTPS requests.
Software & Technique
I used Fiddler Everywhere4 v1.6.0, Mozilla Firefox5, Ubuntu 21.046 and a My.T Internet connection.
Fiddler generated a CA Root certificate which was added to the certificate store of Firefox. Then, Firefox was configured to use the Fiddler proxy.
All web requests, i.e HTTP and HTTPS requests, were intercepted by the proxy. HTTPS requests to and from different websites were decrypted in real-time.
I used my own Facebook, Messenger, Instagram, Twitter, LinkedIn, Gmail and Hotmail accounts in this experiment.
Results
I sent the photo of a lazy panda to my wife on Facebook to see whether this private message will be decrypted by the proxy.
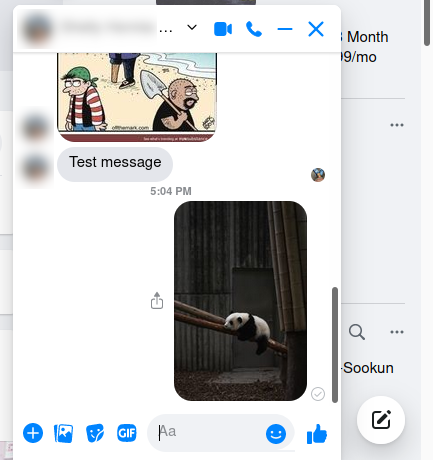
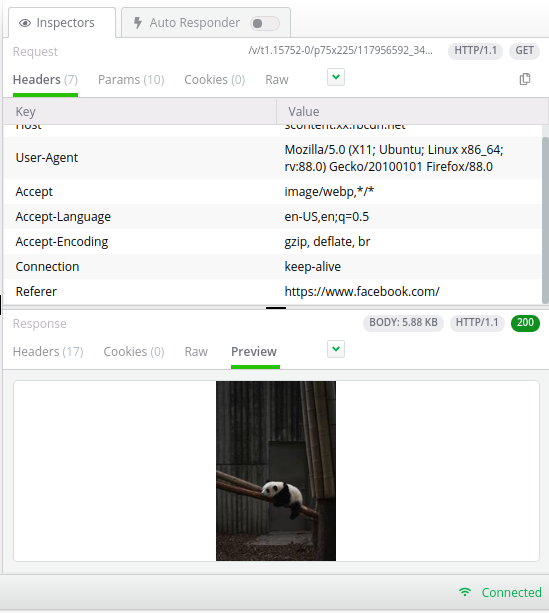
Yes, the private message was decrypted by the Fiddler proxy and the photo appeared exactly as I sent.
Next, I tested messenger.com and the first thing I noted was that the proxy decrypted my login and password.
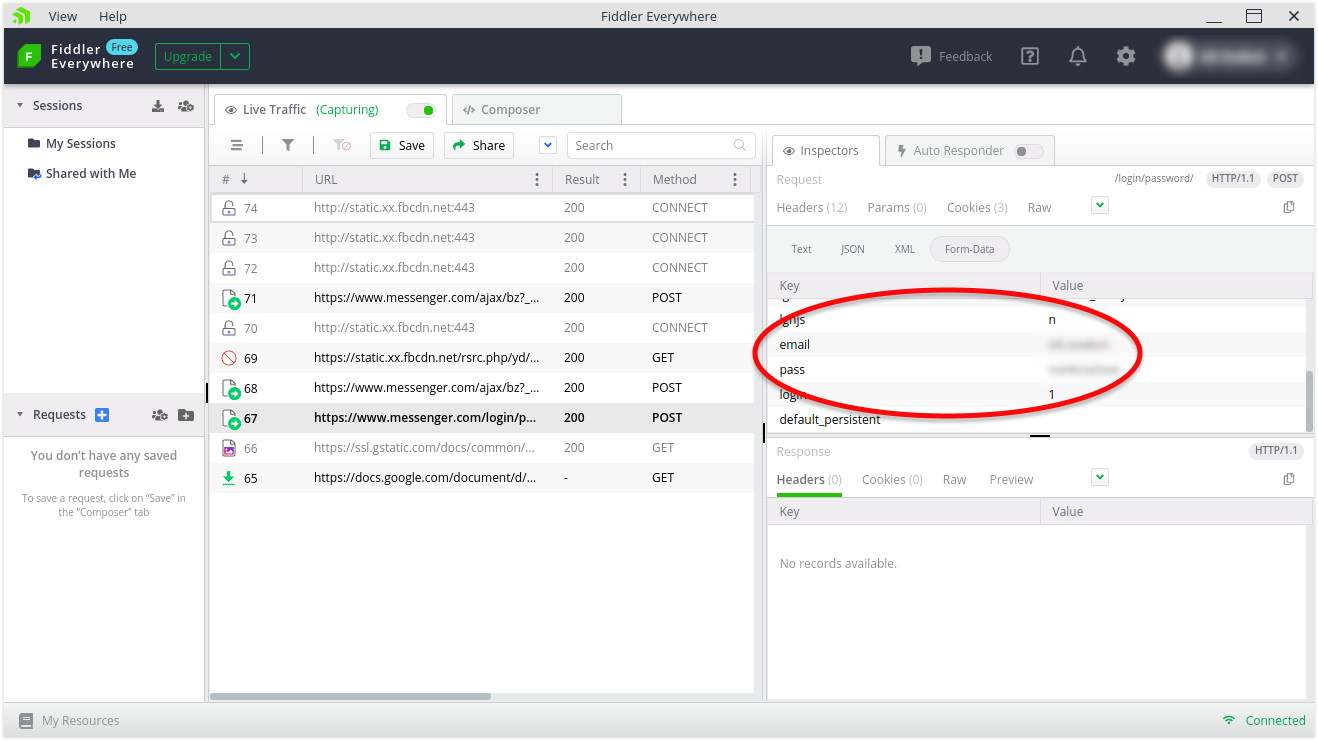
The email field contained the login. Both login and password were exactly what I typed in the login page of messenger.com. I blurred the fields in the screenshot for obvious reasons.
I tested Instagram to see whether a picture that my wife sent me would be decrypted the same way the proxy did for the Facebook private message.
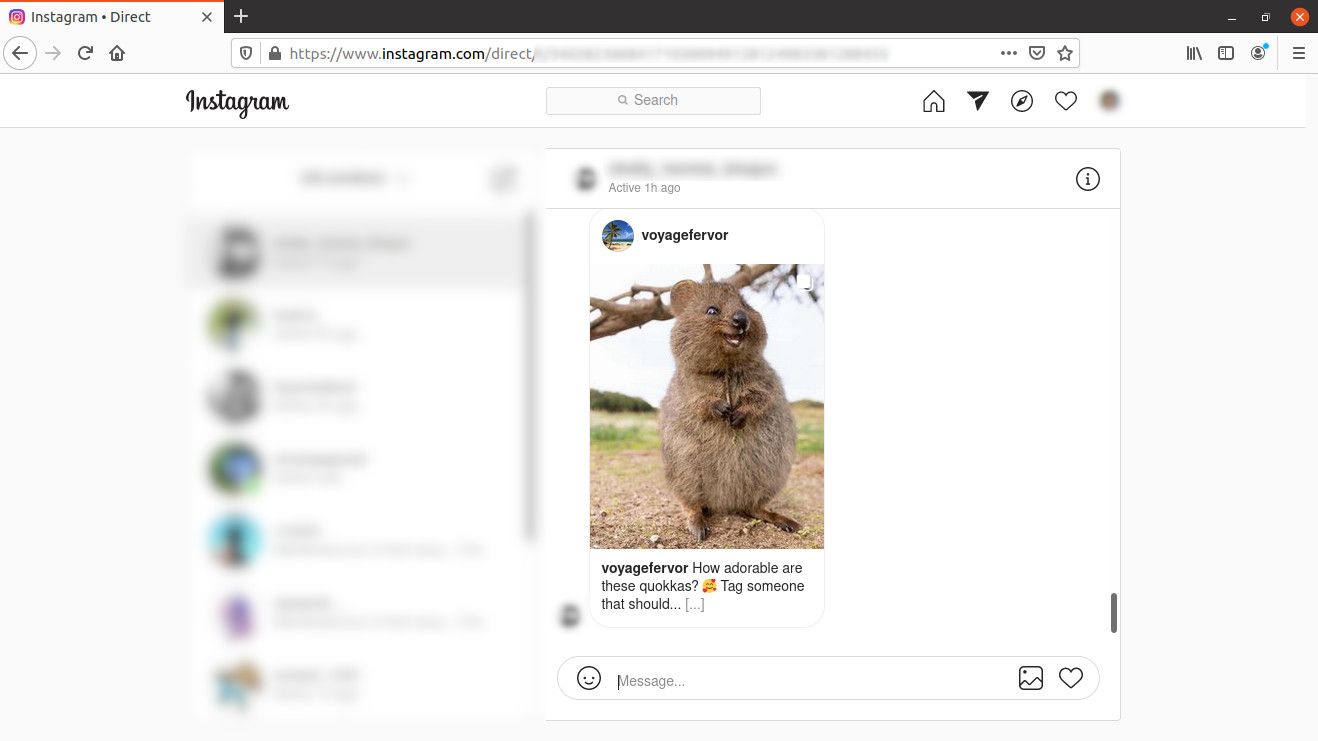
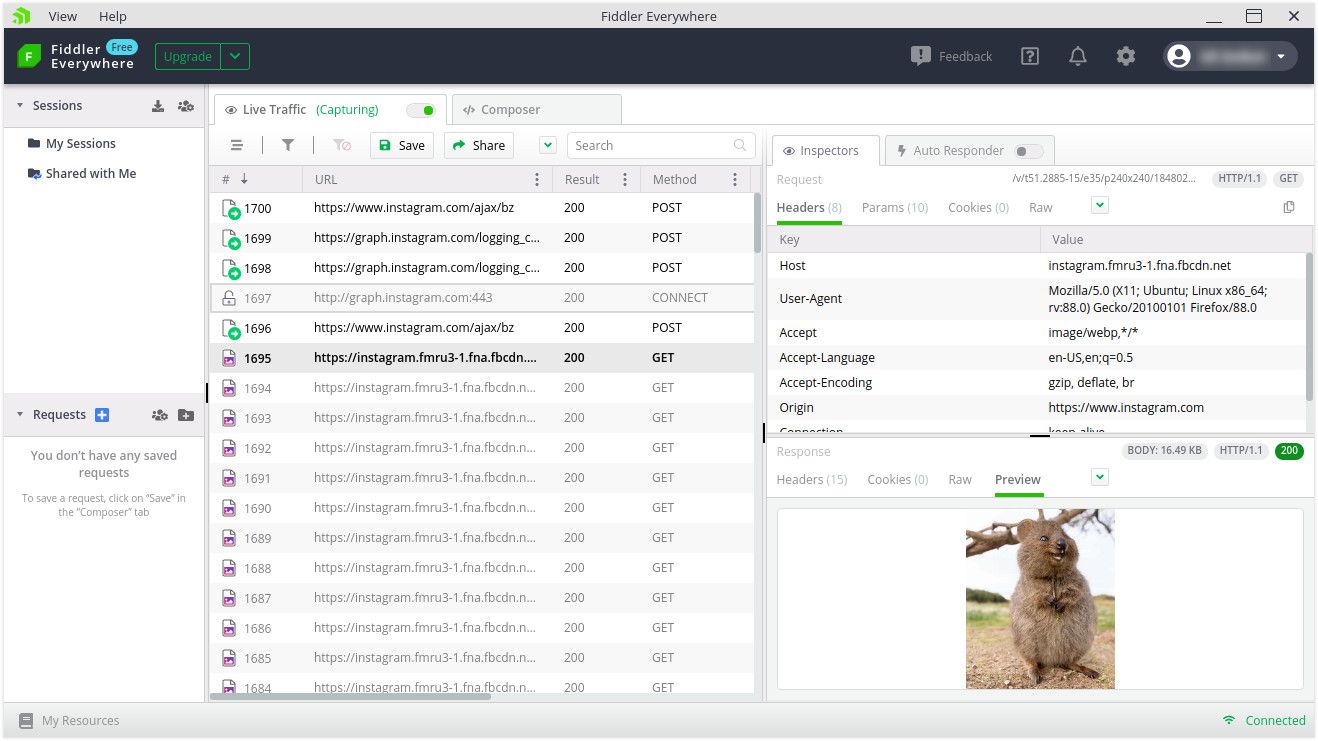
Yes, the picture of the adorable Quokka was decrypted by the proxy, as you may see in the above screenshot.
I tested Twitter and I could see my login, password and direct messages in clear text.
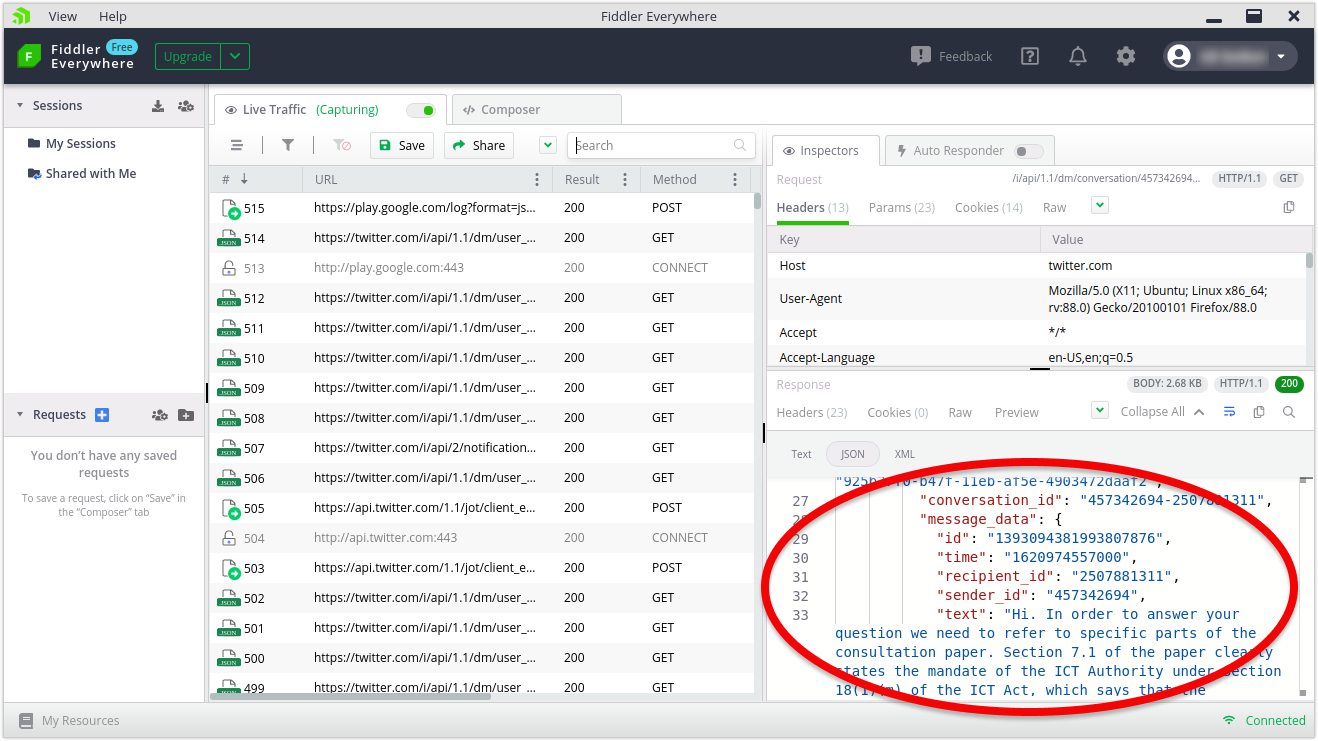
Lastly I tested Gmail, Hotmail and LinkedIn. The login and password of all three platforms appear in clear text.
You will notice that Firefox never prompted me about any untrusted connection while the proxy decrypted the HTTPS traffic.

See above, the padlock will give you the impression that the website is genuine and it can be trusted. However, the certificate is issued by Fiddler and signed with "DO_NOT_TRUST_BC".
Facebook.com is signed by DigiCert and not DO_NOT_TRUST_BC.
Lastly, without decryption there is no way to identify what content the user is accessing on Facebook because all traffic will appear as facebook.com:443.
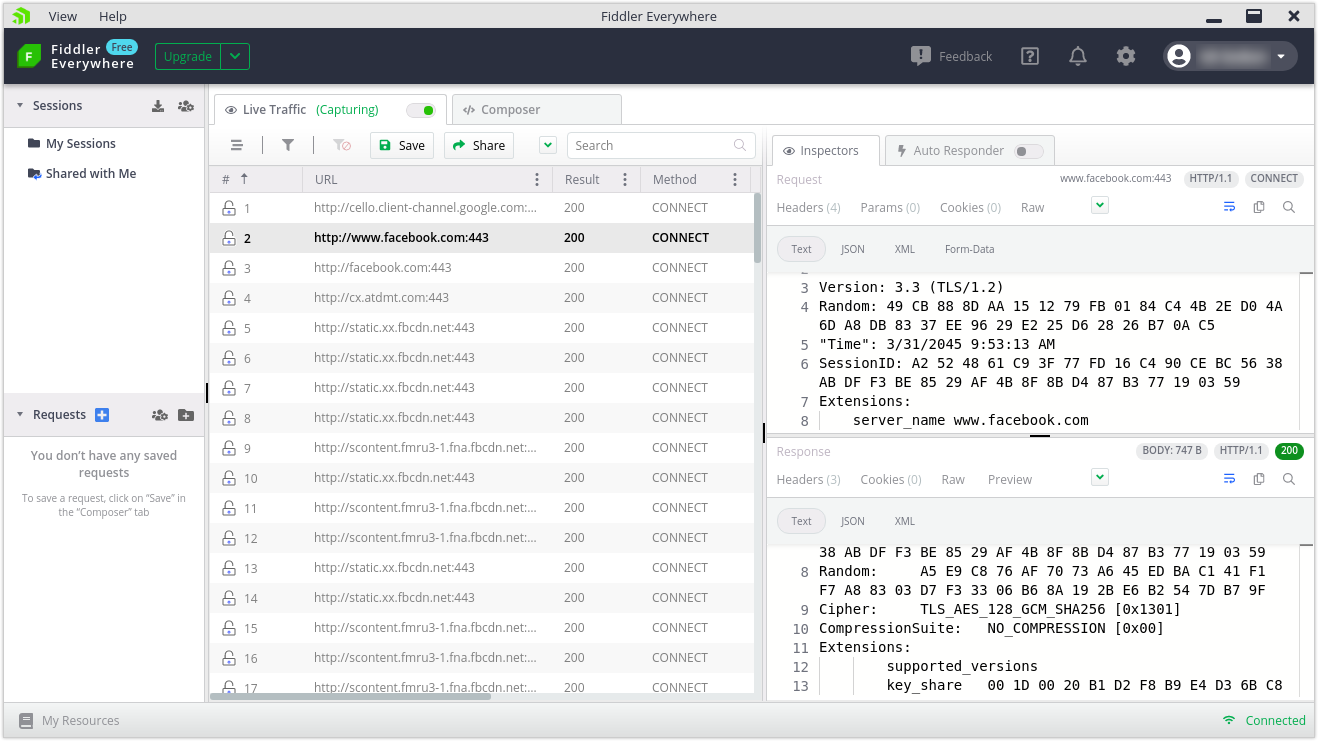
As seen above, all Facebook traffic end with :443 because the complete URL is encrypted. There is no means to know where does facebook.com:443 lead to, whether it leads to facebook.com/public-post or facebook.com/private-content. To obtain the URL information, the entire Facebook traffic will have to be decrypted. This means decrypting login, passwords, public posts and private messages in the process.
Login details, passwords and content sent via private messages can be decrypted by a proxy that is trusted by the web browser. At no point the browser will notify that the website being visited is being proxied and decrypted.
Therefore, if someone starts with decrypting facebook.com today and tomorrow decides to start decrypting gmail.com, the Internet user will not know that this is happening.
Credits to S. Moonesamy for mentioning a proof-of-concept proxy in his slide decks7 on Unsafe Web Browsing in Mauritius.
Cover photo by Etienne Girardet on Unsplash.
- https://www.icta.mu/docs/2021/Social_Media_Public_Consultation.pdf
- https://www.icta.mu/mediaoffice/news2021.htm
- https://www.icta.mu/ICTA_Socialmedia.mp4
- https://docs.telerik.com/fiddler-everywhere/introduction
- https://www.mozilla.org/en-US/firefox/88.0/releasenotes/
- https://discourse.ubuntu.com/t/hirsute-hippo-release-notes/19221
- http://www.elandsys.com/~sm/slides/unsafe-web-browsing-mauritius.html
